Browser Fingerprinting and You
(What It Is, How It Works, How It Violates Your Privacy, and What You Can Do)
Many people use VPNs to protect their privacy by hiding their IP address. Websites, hackers, advertisers, and ISPs can’t track your geo-location and digital footprints anymore, so it’s all good, right?
That’s true, but what about the other ways sites can track you? Like cookies and browser fingerprinting?
We already have a guide detailing how cookies affect your privacy, and how you can deal with them. In this article, we’ll focus on browser fingerprinting, a much more invasive and creepy way websites can keep tabs on you.
What Is Browser Fingerprinting?
It’s a method websites use to track visitors across the web by assigning a unique identifier (the “fingerprint”) to them. It contains a ton of data that can be matched against the browser characteristics of known people. Also, browser fingerprinting allows websites to link online behavior patterns to specific users.
It’s pretty similar to how police analyze fingerprints. They collect them from a crime scene and match them against a whole database of fingerprints to determine who they belong to.
Only in this case, you’re not a criminal. Instead, you’re basically the product of data mining.
What Data Does Browser Fingerprinting Collect?
We’ve heard a lot of people say browser fingerprinting is possible because websites see your IP address. Hide it, and it’s no longer an issue.
Unfortunately, it’s not as simple as that. Yes, browser fingerprinting collects IP addresses, but it doesn’t stop there. In fact, this tracking method doesn’t even need your IP address to keep tabs on you.
According to the EFF’s (Electronic Frontier Foundation) own research, this is the kind of data that are collected:
- The user agent (a string of data revealing the browser and OS versions, device type, language, toolbars, and sometimes more information)
- The timezone
- Your screen resolution and its color depth
- Supercookies
- Whether or not you have cookies enabled
- System fonts
- Browser plugins + plugin versions
- Browsing history
Don’t think it’s a big deal?
Well, the EFF’s research found that there’s a very small chance you’ll have a 100% match with a different browser. To be exact, only one in 286,777 other browsers will share the same fingerprint with another user.
Translated, that means there’s a very big chance your browser fingerprint will be unique and stand out.
Additional research also found that a certain type of browser fingerprinting can identify users behind one browser and users who use multiple browsers on the same device. Apparently, it can identify 99.24% of users, and removing any feature from it will only decrease the accuracy by around 0.3%.
Oh, and the information we listed here is just what the EFF enumerated in their experiment. If you run a browser fingerprinting test (we’ll get to that in a bit), you’ll see there’s much, much more data collected.
How Browser Fingerprinting Works
This process is possible because your browser shares data with a web server when you connect to a website. Because websites can’t assign that data to a specific person, they usually assign a unique browser fingerprinting code to you.
Something like “gh5d443ghjflr123ff556ggf,” for example.
That string of random numbers and letters will help the web server recognize you, and associate browsing behavior and preferences with you. Anything else you do online will also be linked to that unique code.
For instance, if you log into Twitter, and you have real information about yourself there, all that data will be linked to the identifier.
You won’t have that code assigned to you all your life, though. You’ll eventually use a different device or browser, and you’ll get a new one.
How Do Sites Collect Browser Fingerprinting Data?
It happens on two levels – server-side and client-side:
Server-Side Logging
Web servers use the following to collect data about you:
Website Access Logs
They collect data sent by your browser and can be configured to log a lot of information. At a minimum, though, they collect the following:
- The requested protocol;
- The requested URL;
- Your IP address;
- The referer;
- The user agent.
Headers
Web servers receive them from your browser. Headers are vital because they make sure a site works with your browser.
For example, the information in a header lets a website know if you’re using a mobile device. In that case, the site redirects you to its mobile-optimized version. Unfortunately, that same data also contributes to your unique fingerprint.
Cookies
Web servers will always exchange cookies with your browser. If you accept them, they end up on your device and get sent back to the server whenever you reaccess the site.
Cookies generally help websites deliver a better experience, but also help them learn more about you.
Canvas Fingerprinting
This method uses the HTML5 canvas element, which WebGL also uses to render 2D and 3D graphics in a browser.
Canvas fingerprinting actually forces your browser to render graphic content – image, text, or mix of both. You’ll never see it, though, because it’s hidden in the background.
Since different devices have different compression and rendering methods, fonts, and color profiles, the rendered graphic is always slightly different for each browser.
Once finished, canvas fingerprinting turns the graphic into a hash, which becomes the unique fingerprinting code we mentioned before.
Overall, this method allows web servers to learn specific information about your device’s:
- Graphics card;
- Graphics driver;
- GPU;
- CPU (if you don’t have a dedicated graphics card);
- Installed fonts.
Client-Side Logging
“Client-side” just means your browser, who also willingly shares a lot of data with web sites thanks to:
Adobe Flash and JavaScript
According to AmIUnique’s FAQs, if you have JavaScript enabled on your browser, it gives out information about the plugins you use or your hardware specifications.
Similarly, if you have Flash installed and enabled, its API allows web servers to log a lot of data:
- What timezone you’re in.
- The OS version you’re running.
- Your device’s screen resolution.
- A complete list of fonts.
Cookies
Alongside server-side logging, they play an important role in client-side logging too. You’re the one who decides if your browser will accept cookies or clear them from your device.
If you allow them, web servers learn a great deal about your device and preferences. If you don’t accept cookies, sites will still receive data from your browser, notifying them about that. Ironically, that will likely make your fingerprint stand out even more.
Why Is Browser Fingerprinting Used?
Primarily, to make sure you get the right website version on your device – like the tablet version on your iPad.
Besides that, we also speculate it’s used for advertising purposes. It involves a great deal of data mining, after all.
And with this kind of information, advertisers can craft very targeted and personalized profiles for specific market segments. Significantly more in-depth than what they would have if they were to only focus on IP addresses.
Here’s one example we thought of – advertisers could use browser fingerprinting to single out users with a small screen resolution (like 1300 x 678) who are browsing higher-resolution monitors on an eCommerce site. Or users who are just browsing the site in general, and not looking for anything in particular.
They can then use that data to target those people with ads for higher-resolution monitors. They could do it in a pretty aggressive and invasive way by crafting extremely relevant (and simultaneously creepy) marketing copy that specifically mentions their current screen resolution.
Besides that, we believe browser fingerprinting has other use cases:
- To detect fraud and botnets. It really comes in handy for banking and dating sites since they’d be able to detect suspicious behavior by seeing it’s coming from multiple, different locations and devices.
- To detect VPN and proxy users. Surveillance agencies can use this tracking method to spot Internet users who are hiding their geolocation. After all, browser fingerprinting will reveal the same device characteristics, but a different IP address. Or a time zone that doesn’t correspond to the IP address.
Ultimately, even if browser fingerprinting has legitimate uses, it’s still very bad for your privacy – especially if you are actively trying to protect it by using a VPN.
Also, fingerprints can be a hacker’s best friend. If they know your device’s exact details, they can use specific exploits to target you. And really, any cybercriminal can set up a fake site with a fingerprinting script.
Is Browser Fingerprinting Legal?
We heavily researched this topic, but couldn’t find any specific laws about browser fingerprinting. If you happen to know about particular laws in your country that regulate fingerprinting, let us know.
With that said, the GDPR and ePrivacy Directive in the EU likely dictate how sites can use browser fingerprinting. It’s not illegal, but any entity that processes personal data needs to prove they have a legal reason to do it.
Also, they need to get user consent first. There are two exceptions, though:
- When fingerprinting is needed for “the sole purpose of carrying out the transmission of a communication over an electronic communications network.”
- When fingerprinting is needed to customize the user interface for a specific device. For example, when you use a mobile device to browse a site, it uses fingerprinting to send you to the mobile-optimized version.
We assume similar rules apply in other countries. So the bottom line is that sites need your consent for browser fingerprinting.
But here’s the problem – they don’t make it obvious. Sites hide any stuff about “fingerprinting” in long, boring ToS and Privacy Policy pages. And they don’t mention fingerprinting at all in banners or on “I agree to the terms of service” pop-ups.
So you usually consent to browser fingerprinting whenever you browse a site and agree to its terms.
How to Run a Browser Fingerprinting Test
Alright, so we talked about how much data this identification method collects. But how do you check what specific information sites have on you in particular?
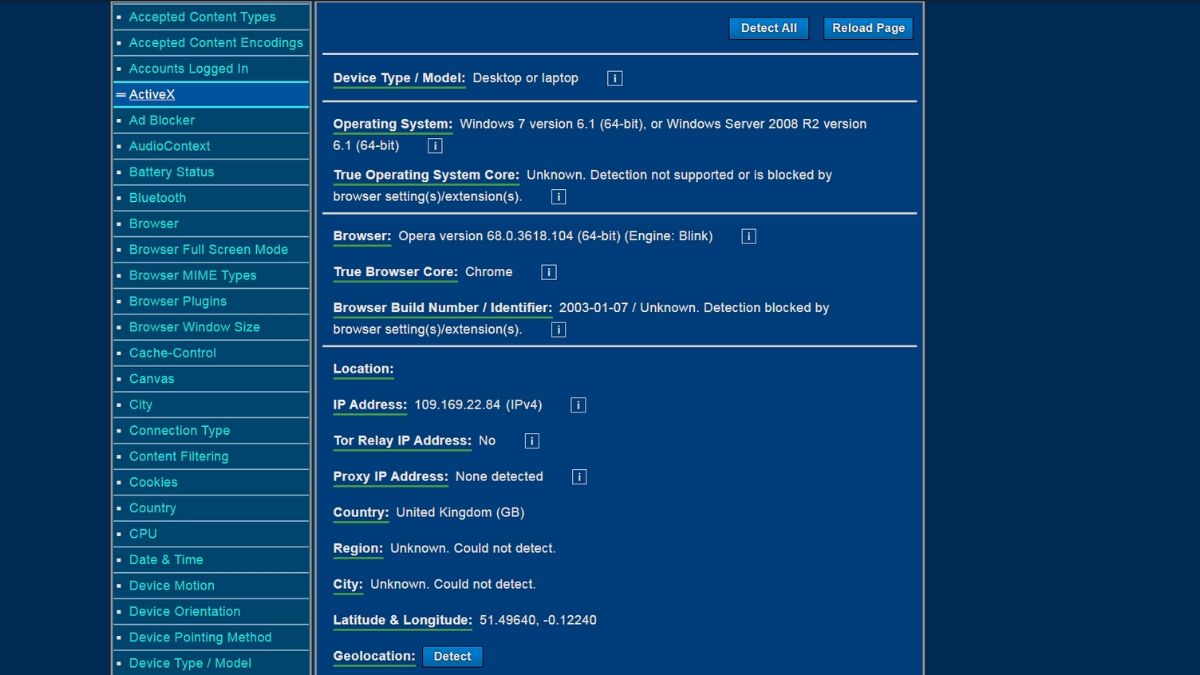
By far, the easiest way to do that is with Device Info – a browser fingerprinting test site.
See the list on the left? It keeps going as you scroll down. And the only reason our city and region don’t show up is that we used a VPN.
Besides Device Info, there’s also Panopticlick from the EFF and AmIUnique that is open-source. They’re both pretty great tools, but Device Info is the most user-friendly (at least in our opinion).
What Is Browser Fingerprint Entropy?
It’s a measure of how unique your browser fingerprint is. The higher the entropy, the more unique it is (so, the more you stand out).
Fingerprint entropy is measured in bits. So if you use Panopticlick and the results sais “we estimate that your browser has a fingerprint that conveys at least 17.87 bits of identifying information,” then that’s your fingerprint entropy.
How Accurate Are Browser Fingerprinting Tests?
Well, they provide accurate information about your browser and device, and they definitely show you what data sites collect.
But fingerprint tests are not 100% accurate when they estimate your fingerprint entropy. Here’s why:
- They don’t really account for randomized fingerprints. For example, if you use Brave Nightly, your fingerprint will be randomized every time you visit a site.
- Test sites like Panopticlick and AmIUnique have huge databases that contain information about old and outdated browsers. So if you run a test with a new browser, you’re more likely to get a high entropy result – even though there are dozens of other people using the same browser type and version.
- Lastly, they don’t account for screen resolution or browser screen size changes. Maybe the fonts are too small, or the font colors are hard to read up close. Whatever the reason, browser fingerprinting tests don’t account for that. So every small change in resolution or window size is detected as a measure of how unique you are, which is pretty misleading, in our opinion.
Now we’re not saying these tests aren’t useful. By all means, you should definitely use them to find out what unique information about you is available on the Internet.
But you shouldn’t try running them every time you make a change to see if you get a lower entropy score. You’ll just drive yourself mad that way.
How to Protect Yourself Against Browser Fingerprinting (Simple Solutions)
Before we begin, let’s get one thing straight – you can’t completely block browser fingerprinting. The only way to do that is to not use the Internet at all. And that’s not really doable anymore.
But there are some things you can do to make your fingerprint less noticeable. In this section, we’ll take a look at the more “user-friendly” tips you can try:
Use Firefox (And Optimize It)
The Firefox browser is really good at protecting user privacy. And they recently upgraded their browser, making it block third-party fingerprinting resources.
Translated, that means Firefox will block third-party requests to companies associated with browser fingerprinting. That’s really cool because it stops those entities from abusing JavaScript to log data about you. So you don’t need to turn off JavaScript at all.
That’s a great start, but you can do much more with Firefox to further protect your privacy. Start by typing “about:config” in the URL bar and click “Accept the Risk and Continue.” Next, in the search bar, look for the following:
- webgl.disabled – Double-click it to set it to “true.” That should help prevent canvas fingerprinting to some extent.
- geo.enabled – Set it to “false” by double-clicking it. Doing that will prevent geolocation tracking.
- privacy.resistFingerprinting – It’s the first result. Double-click it to set it to “true.” It will offer some basic level of protection against fingerprinting. It’s more efficient if you make all the tweaks on this list, though.
- privacy.firstparty.isolate – Double-click it to change it to “true.” Doing this will isolate cookies from first-party domains.
- media.peerconnection.enabled – This isn’t mandatory, but you can set it to “false” if you use a VPN since it will prevent WebRTC leaks, which can reveal your IP address.
See More: The Complete Guide to WebRTC (What It Is, How It Works, How Safe It Is, and How to Handle Leaks)
Use Brave
If you want a Firefox alternative, the Brave browser is a good option. It’s very privacy-friendly – it blocks cross-site trackers, automatically upgrades your connections to HTTPS, and can even block scripts.
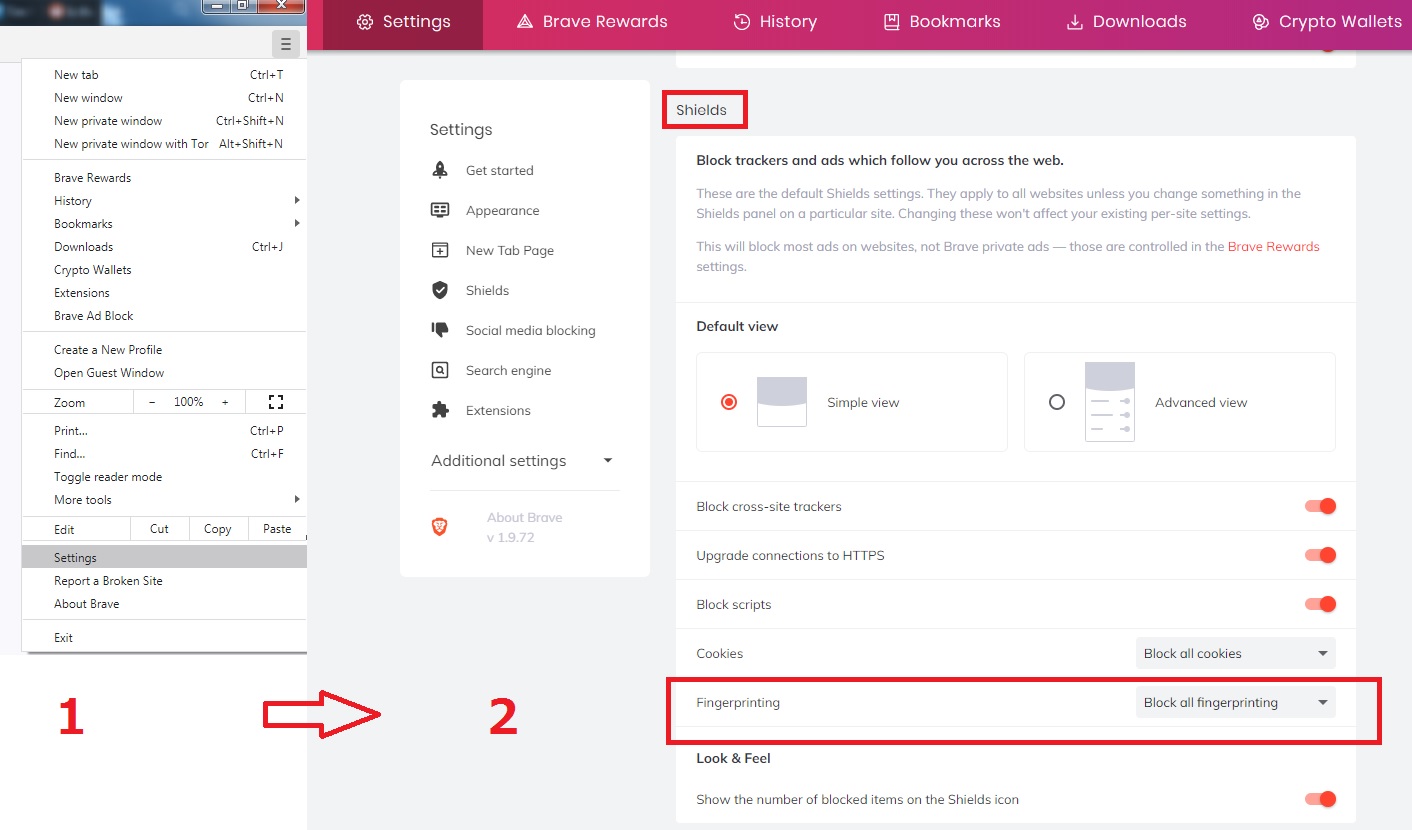
Besides that, Brave lets you block all fingerprinting. Just head to “Settings,” scroll down to “Shields,” and set “Fingerprinting” to “Block all fingerprinting.”
We used Panopticlick to test Brave with that option enabled. Compared to our original browser (Opera), the entropy level was slightly smaller (16.31 bits instead of 17.89 bits). Not a huge difference, but it’s not bad either.
There’s a lot to discuss when it comes to Brave’s browser fingerprinting protection. We don’t want to bore you with all the technical details, so feel free to check them out here when you have the time.
Use Anti-Fingerprinting Extensions
Extensions are tricky because they can sometimes make your fingerprint more unique. We didn’t get higher entropy levels with the extensions we’ll mention here. But results can vary from user to user, so some people might get higher entropy results.
It’s really all about testing out the extensions to see which one makes you stand out the least.
With that out of the way, here are the extensions we recommend trying:
- Chameleon – An extension that lets you spoof user agent values. You can even set them to change periodically (like every 10 minutes).
- Trace – This extension should protect you against different browser fingerprinting techniques.
- User-Agent Switcher – Similar to Chameleon, it spoofs user agent data. Here’s the GitLab link.
- Canvasblocker – It keeps you safe from canvas fingerprinting. Here’s the download link for Firefox.
We recommend sticking with just one extension, if possible. The more you use, the more unique you’ll be.
Disable Flash
Flash reveals a lot of data about you, and it’s likely going to be gone soon. If you use the latest browser versions, you don’t need to do anything. They all disable Flash by default.
If you use older versions, though, here’s what you need to do:
- For Firefox, go to “Add-ons,” then “Plugins,” and choose “Never Activate” for the Shockwave Flash plugin.
- For any Chromium browser, go to “Settings,” and type “Flash” in the search bar. You’ll usually reach “Site Settings,” and you can select an option that stops all sites from using Flash.
Disable JavaScript
Like Flash, JavaScript shares a lot of sensitive data about your browser and device with web servers. It’s a good idea to disable it, but keep in mind some websites won’t work properly because they rely on it.
As far as we can tell, Brave disables JavaScript by default. At least we can’t find any guides on how to disable it, just people asking how to enable it.
For other browsers, here’s what you need to do:
- Firefox – Type “about:config” in the URL bar, click “Accept the Risk and Continue,” and then type “javascript.enabled” in the search bar. Double-click it to switch it to “false.”
- Chromium browsers – Just head to “Settings,” and type “JavaScript” in the search bar. Again, you’ll usually be taken to “Site Settings.” There, you can set JavaScript to “Blocked.”
Alternatively, just use NoScript. You can even configure it to allow JavaScript on sites you really need to work well. Alternatively, use uMatrix cause it also disables JavaScript.
Use the Tor Browser Without the Tor Network
The Tor browser is like Firefox on steroids. It offers a ton of features that protect your privacy by default:
- HTTPS Everywhere
- NoScript
- Blocks WebGL
- Blocks canvas image extraction
- Cloaks your OS (fingerprinting reveals Windows 7 for all Tor users)
- Blocks timezone and language preferences
- Anti-tracking features
Also, you’ll have the same fingerprint as all Tor users as long as you don’t change the default browser windows size.
But the Tor network isn’t as amazing as the Tor browser. Here’s why:
- It has very slow speeds. With only around 6,000 servers for roughly two million users, that’s hardly surprising.
- Many sites block Tor traffic – like Netflix, for example.
- Tor suffered serious IP leaks in 2017. And Windows users are still susceptible to IP leaks in certain situations.
- You can’t torrent over Tor. The devs don’t recommend it, and some torrent clients can leak your IP address. Plus, the slow speeds don’t help.
- Tor has a weird relationship with the US government – they cooperate with it and receive funding from it.
- You can be unlucky enough to come across a malicious node.
All in all, you’re better off only with the browser if you care about your privacy.
Now, disabling the Tor network on the browser is a little tricky. But don’t worry – we kept it simple so that anyone can do this. Most online guides will say you need to make a few changes in about:config and the menu, but that no longer works with the latest version. You need to create two files to force the browser to disable the Tor network.
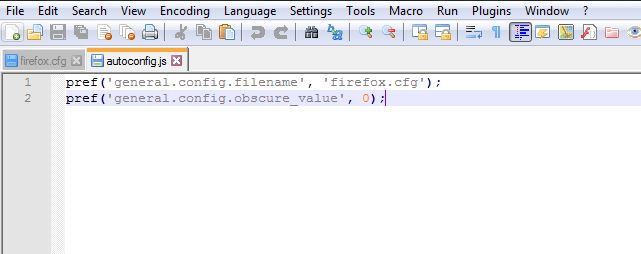
For starters, you’ll need Notepad++. Open it, and copy these two lines in a new tab:
pref(‘general.config.filename’, ‘firefox.cfg’);
pref(‘general.config.obscure_value’, 0);
Go to Edit > EOL Conversion, and choose “Unix (LF).” Now save the file as “autoconfig.js” (save as “All types” not “Normal text file”) to this directory “Tor Browser > defaults > pref.”
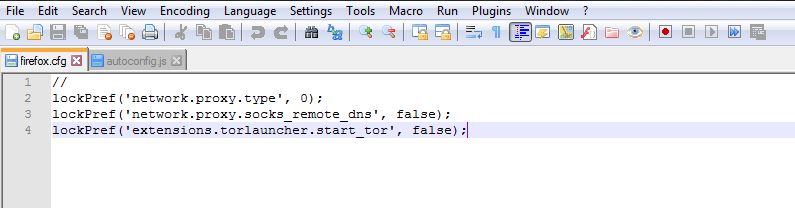
Next, open another tab, and copy these lines:
//
lockPref(‘network.proxy.type’, 0);
lockPref(‘network.proxy.socks_remote_dns’, false);
lockPref(‘extensions.torlauncher.start_tor’, false);
Yes, including the “//”
No need for the LF conversion since it’s already enabled from before. Save the file as “firefox.cfg” (again, as “All types”) to “Tor Browser > Browser”, where you have “firefox.exe.”
And you’re done. Whenever you run the Tor browser now, you won’t get any loading screen, and you’ll see this:
Just ignore the warning, and start browsing. Ideally, use a VPN for even more privacy.
And no, disabling the Tor network won’t affect your fingerprint. We tested the browser without the network with Panopticlick and got an entropy level of 10.3 bits – much lower than what we had with Brave (16.31 bits).
If the files don’t work, it could be because our site uses a different font, and the punctuation marks (; or ‘) weren’t copied right. Just delete them and type them yourself.
Alternatively, download them right here. We uploaded a .zip archive with the two files to MEGA. Feel free to scan it with your antivirus before unzipping the files if you want. After you unzip them, copy them to these directories (we’ll assume you installed Tor in C):
- firefox.cfg – C:Tor BrowserBrowser
- autoconfig.js – C:Tor BrowserBrowserdefaultspref
If you have any problems, let us know. Also, if you find new ways to disable the Tor network on the browser, go ahead and leave the instructions in the comments.
How to Protect Yourself Against Browser Fingerprinting (Hardcore Tips)
We made this separate section because not all of you will want to try out these things. These tips are more complicated, and you’ll probably only want to try them if you’re really obsessed with protecting your privacy.
So, let’s get started:
Use Firefox with the user.js File from ghacks
The user.js file is a configuration file that controls many Firefox settings. The file from ghacks is optimized for privacy and security, so you don’t need to manually handle about:config tweaks.
Also, ghacks’ file receives regular updates, which is very helpful.
We mentioned this tip here instead of earlier in the article because there’s a lot of documentation to go through before you use this file. Here’s the guide you need to read through.
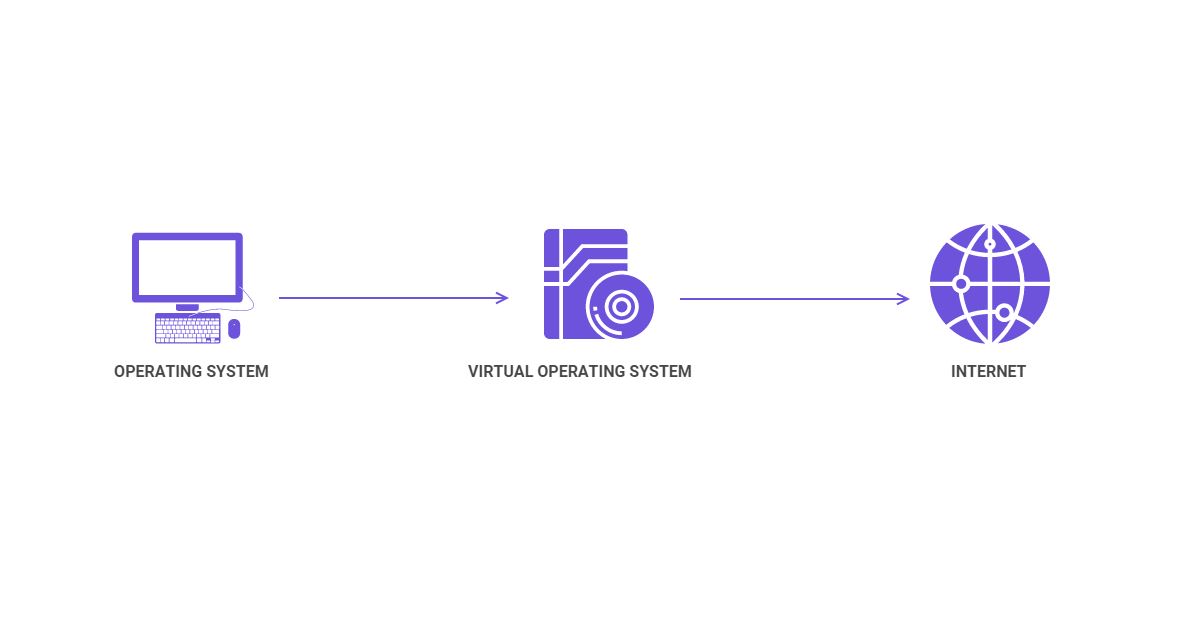
Use a VM (Virtual Machine)
A VM is a virtual operating system you run on top of your existing OS. For example, you run Windows 10, and use a VM to run a virtual Linux distribution or Windows 7 on top of it.
VMs can reduce your fingerprint entropy by preventing sites from fingerprinting details about your OS and hardware. You will connect to web servers using the VM, so they’ll only collect data associated with it (much like websites only see a VPN server’s IP address, not your real address).
The VM’s “hardware” (RAM, GPU, CPU) is emulated, so web servers don’t gather any relevant data that could compromise your privacy.
Here are the best VM services (in our opinion):
- VirtualBox (Windows, Linux, macOS, Solaris)
- VMware Workstation Player (Windows, Linux)
- VMware Fusion (macOS)
- Parallels Desktop (macOS)
- Hyper-V (Windows)
There’s not much to say about setting up the VM. Most services will have a tutorial, but you only need to install it and run it before going online. You’ll, of course, need to get licenses for paid OSs, but you could always use a free one, like Ubuntu.
Related: How to Combine VPNs, Tor & Virtual Machines? – Create the Ultimate Online Anonymity Tools Arsenal!
Avoid Smartphones
Smartphones are very convenient, but they’re extremely vulnerable to fingerprinting – much more than other devices. Researchers from Cambridge published a paper detailing just how bad things are.
Here’s the link for the research and the link for a quick overview of their findings.
If you don’t have time to read them, here’s what you need to know:
- Smartphones are very vulnerable to calibration fingerprinting attacks.
- Any site or app can use this attack if you have a vulnerable device. And they don’t need your consent to do it.
- This attack can generate a fingerprint in less than one second.
- The attack can generate unique fingerprints for any iOS device.
- This attack can easily track you across sites and apps.
- Even if you do a factory reset, the fingerprint won’t change.
Apple says they fixed this issue with iOS 12.2. Google has yet to resolve the issue as far as we know, though.
Vulnerabilities like this one will likely keep popping up, so avoiding smartphones is the best option if you are concerned about this. At the very least, consider using an iOS smartphone instead of an Android one if ditching smartphones isn’t an option.
Use Separate/Burner Devices
Pretty extreme, but if you can afford to do this, it’s another layer of privacy you put between you and fingerprinting.
Here’s the idea – you would get a separate device (like a laptop) which you use for general internet browsing (like reading Reddit posts or posting on Twitter).
For personal stuff (email, bank account, PayPal, etc.), you would use a different device. Ideally, you should run a VM on it, and use all the other tips we mentioned in this article.
If you’re very “paranoid,” as some people would put it, you could use burner devices that you replace every few months or every year.
Exaggerated? Maybe, but it will definitely make it harder for anyone to notice common patterns between your online activities.
Separate Your Private Online Life from Your Public One
Most people would tell you to just use different browsers simultaneously – like Firefox for Facebook and Opera for Twitter. That’s a good start, but it’s not enough. It’s actually possible for sites to fingerprint you even if you use multiple browsers.
Instead, you should use one browser for public activities (social media, talking with your friends, googling random things, work, etc.), and a different browser for private activities (online banking, in-depth research, crypto trading, etc.).
That’s not all – you should also use separate usernames, email addresses, and passwords for your public and private online life. It’s safer in general, but it also stops you from leaving a trail of breadcrumbs that can identify you.
Doing this won’t stop browser fingerprinting completely. But it might stop web servers and people from correlating your public online life to your private one.
Can a VPN Protect You Against Browser Fingerprinting?
We’ve heard many people say that using a VPN protects you against fingerprinting. We hate to be a buzzkill, but that’s not really true.
A VPN can offer some protection, but it’s very minimal. The only thing it can do for you is to hide your IP address. But it can’t stop sites from using fingerprinting to gather other data – like your OS and browser version, language preferences, or timezone.
Basically, if you only rely on a VPN, your entropy levels won’t go down at all. We ran a browser fingerprinting test with and without a VPN, and had the same entropy level.
Should You Still Use a VPN Then?
Of course. It might not stop fingerprinting, but it still does wonders for your online privacy.
Besides hiding your IP address, VPNs also encrypt your traffic. ISPs, hackers, and government surveillance agencies won’t be able to monitor it anymore. Instead of seeing your unencrypted DNS queries, they’ll only see gibberish (“34FHkdiwz56hFDHFldsijd3” instead of “facebook.com,” for example).
In the end, going through all the trouble of using the tips in this article to reduce your fingerprint entropy is pretty pointless if your ISP can monitor your traffic and sell your browsing data to advertisers.
So make sure you use a VPN on top of following the pointers we offered so far. If you need recommendations, check out ExpressVPN, CyberGhost VPN, NordVPN or Surfshark. Alternatively, see our guide to the best VPN services for more information.
Does Incognito Mode Stop Browser Fingerprinting?
No, it won’t do anything to protect you from it. Sure, incognito mode will keep your browsing private from anyone you share the device with by clearing your browsing history. Also, it will delete most cookies, so you get a certain level of privacy.
But it can’t spoof your user agent, language, screen size, installed plugins, or timezone. Any site you connect to will still log all that data (and more).
If you don’t believe us, go ahead and test your fingerprint with and without incognito mode. In our tests, we had the same entropy level.
How Do You Like to Lower Your Fingerprint Entropy?
Do you follow the tips we covered in this article, or do you rely on other methods? If you do, are they effective? If yes, go ahead and share them with us in the comments or on social media.
Similarly, if we missed any information about browser fingerprinting, let us know. We’ll be glad to include more relevant information in the article.
M3u Iptv Romania Playlist All Channels 1/10/2020(Opens in a new browser tab)
Free Daily IPTV Canada M3u Playlists 11/10/2020(Opens in a new browser tab)
LazyMan Kodi Addon(Opens in a new browser tab)
Free IPTV LINKS M3u Playlist 11-10-2020(Opens in a new browser tab)





0 Comments